Crypto Talk at 27C3: New Key Recovery Attacks on RC4/WEP, Day 4, 17:15, Saal 2
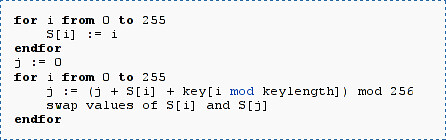 The RC4 Stream Cipher could be the most common stream cipher used on the Internet. RC4 is the only Stream Cipher which is standardized for the SSL/TLS protocol, it is also used for WEP and WPA protected wireless networks. Initially, RC4 was designed to be a closed source commercial product, with the core algorithm kept secret. In 1994, the source code for RC4 was posted on the internet and the algorithm could be analyzed.
The RC4 Stream Cipher could be the most common stream cipher used on the Internet. RC4 is the only Stream Cipher which is standardized for the SSL/TLS protocol, it is also used for WEP and WPA protected wireless networks. Initially, RC4 was designed to be a closed source commercial product, with the core algorithm kept secret. In 1994, the source code for RC4 was posted on the internet and the algorithm could be analyzed.
The first attack on RC4 was published by Fluhrer, Mantin, and Shamir in 2001. The attack is very effective, but can only be used against certain keys starting with a special …







