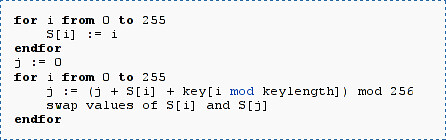
We Came in Peace: Event Recordings Available!
It’s only been a few days since the close of the 27c3, but much of the conference is ready to download. Credit goes in no small part to the FEM, who did a really tremendous job during the conference and continue their hard work getting Official Releases of the talks ready to go.
 If you enjoyed the streams and the recordings of the talks, consider [supporting their efforts][5] to purchase updated equipment to improve the image quality and transmission path for future events.
If you enjoyed the streams and the recordings of the talks, consider [supporting their efforts][5] to purchase updated equipment to improve the image quality and transmission path for future events.
Did you really love certain events? Weren’t so excited about others? Let us know! You can leave feedback via the …