-
13:30
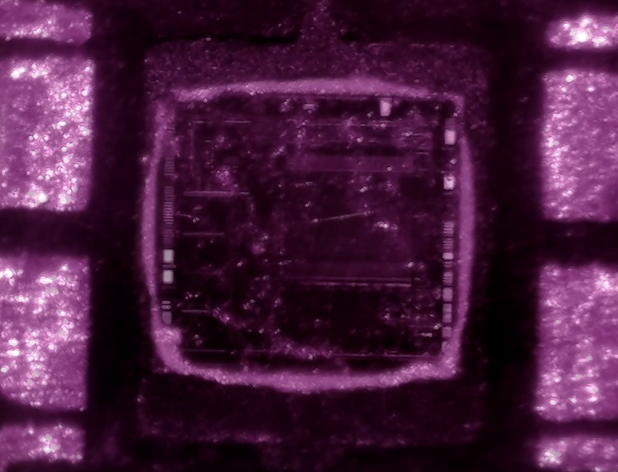
Stored memory in hardware has had a long history of being influenced by light, by design. For instance, as memory is represented by the series of transistors, and their physical state represents 1's and 0's, original EPROM memory could be erased via the utilization of UV light, in preparation for flashing new memory.
Naturally, whilst useful, this also has proven to be an avenue of opportunity to be leveraged by attackers, allowing them to selectively influence memory via a host of optical/light-based techniques. As chips became more advanced, the usage of opaque resin was used as a "temporary" measure to combat this flaw, by coating chips in a material that would reflect undesirable UV.
Present day opinions are that laser (or light) based hardware attacks, are something that only nation state actors are capable of doing; due to both limitations of cost in tooling as well as personnel expertise required. Currently, sophisticated hardware labs use expensive, high frequency IR beams to penetrate the resin.
This project demonstrates that with a limited budget and hacker-and-maker mentality, similar results can be obtained at a fraction of the cost, from the comfort of your home or garage. With the modifications of an opensource low-cost microscope, addition of a home-built beam splitter and interchangeable diode laser, it has been shown that consumer-grade diodes are capable of producing results similar to the high-cost variants, such as the YAG lasers.
One example of results includes introducing affordable avenues to conduct laser-based fault injection, via the usage of such budget-friendly tooling. We are opening the study of these low-level hardware attacking methodologies to more entry-level security testers, without the need for hundreds of thousands of dollars in startup capital.
By leveraging more affordable technology alternatives, we have embarked on a mission to uncover hardware malware, detect supply-chain chip replacements, and delve into the realm of laser-logic-state imaging. Our approach integrates optics, laser selection, and machine learning components.