O
2.9-C/3
$natch
| Snatch | |
|---|---|
| Snatch challenge is real-time and “real-life” Internet Banking hacking contest.
Specially for the competition, we developed our own remote banking system from scratch and imbedded common vulnerabilities discovered during of security assessment of such systems... | |
| Type: | Workshop |
| Person organizing | User:Sscherbel, User:Ygoltsev |
| Orga contact | ygoltsev@ptsecurity.ru |
| Starts at | 2012/12/29 03:00:00 PM |
|---|---|
| Ends at | 2012/12/29 05:00:00 PM |
| Duration | 120 minutes |
| Location | Hall 13 |
| Add this event to your calendar (iCal) | |
Latest news
$natch competition is over. Thanks to all the participants!
Right here [[1]] you can find dump of production database. And here [[2]] is a presentation about all the vulnerabilities in our I-Bank system.
And, our winner are:
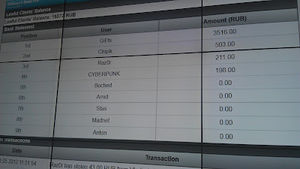
First place - Marcel Mangold (congratz man! you r0ckz!!!) 3038 points
Second place - Julio Cesar (congratz! man, you r0ckz too!!!) 609 points
And Third place -
Tomasz Bukowski, Maximilian Golla, Marcel Kulicolla, BELTT team (guys, next time you should come :))
Thank you for coming! See you!
See you 29 of December, 15:00 Hall 13!
For quick questions - ask me in twitter - @ygoltsev
Woooha! It's first day of 29c3 what means - you can start to find vulnerabilies in I-Bank system. You can download the whole VM image with I-Bank pre-installed from here [[3]] (355 Mb). Also, you can download a full source of I-Bank system from here [[4]] (0.1 Mb). If you have any questions - just ask me via e-mail (ygoltsev[at]ptsecurity.ru) or find me (Yuri) at the CCH location (yellow hoody of CCC, PHDdays 2012 bag).
Note: To access VM's SSH and MySQL use login 'root' and password 'phd2012'.
To register (get your own login and password for production I-Bank system) on the competition - contact me before 11 AM, 29 of December.
Stay tuned!
Disclaimer
$natch challenge is real-time and “real-life” Internet Banking hacking contest. Specially for the competition, we developed our own remote banking system from scratch and imbedded common vulnerabilities discovered during of security assessment of such systems. The solution called PHDays I-Bank is a standard Internet bank with a web interface, PIN code to access the account and a processing. Remote banking vulnerabilities are very different from typical web vulnerabilities (such as XSS or SQL Injection): most vulnerabilities of PHDays I-Bank are logic (such as Race Conditions, One-Time Password prediction, Inefficient Authorization and so on).
The day before the competition the participants will receive an image of an operating system with the installed remote banking (and its source code, of course) and a test base. Thus, they have a day to detect the vulnerabilities and write an exploit for them. During the competition, each participant got their personal login and password to the remote banking system and a real bank card bound with a specific account.
The competition lasted for 30 minutes. The participants were to hack the I-Bank, transfer money to another account. The money can be stolen not only from the “bank” but from other participants as well. Winners will receive gifts from us.
After competition, we can deliver hands-on workshop to demonstrate vulnerabilities, solutions ways to exploit. Winners and participants can join workshop toHall 13 discuss ways they used during competition. Technical details:
- Participants should register at morning of first day of 29C3 and receive VM images of “I-Bank” to find vulnerabilities. You can register right now - just write a message to ygoltsev[at]ptsecurity.ru. This require announcement and maybe personal invitation of skilled web-hackers, because newbies have no chances in this challenge. We can use our communication channels to invite participants.
- Participants at least should have 24 hours to find vulnerabilities and create exploits.
- Challenge will take about 30 minutes. All participants will use own Laptops.
- After challenge we will deliver two hour workshop to demonstrate vulnerabilities used in challenge.
Link http://blog.phdays.com/2012/06/show-me-money-natch-competition-at.html